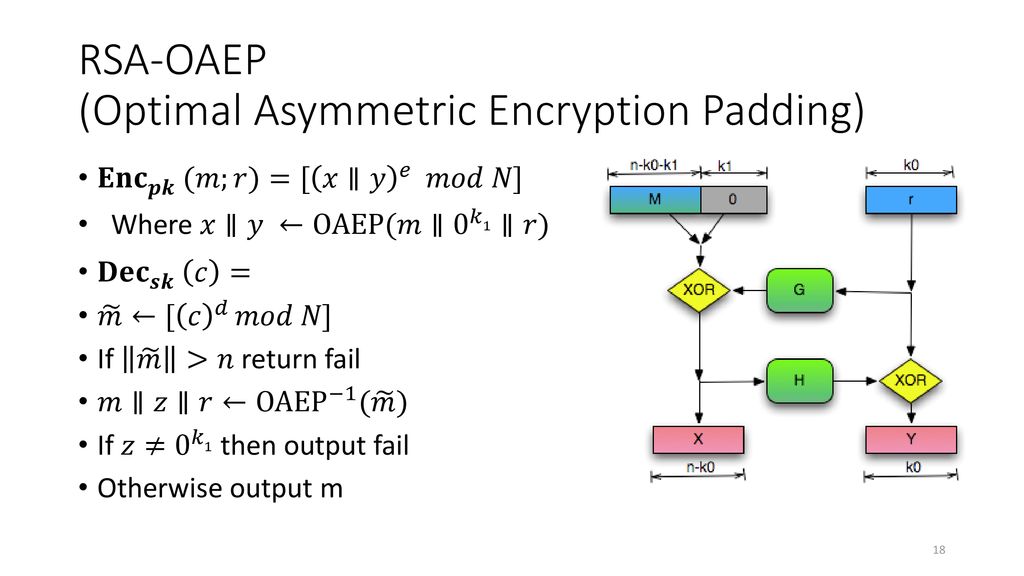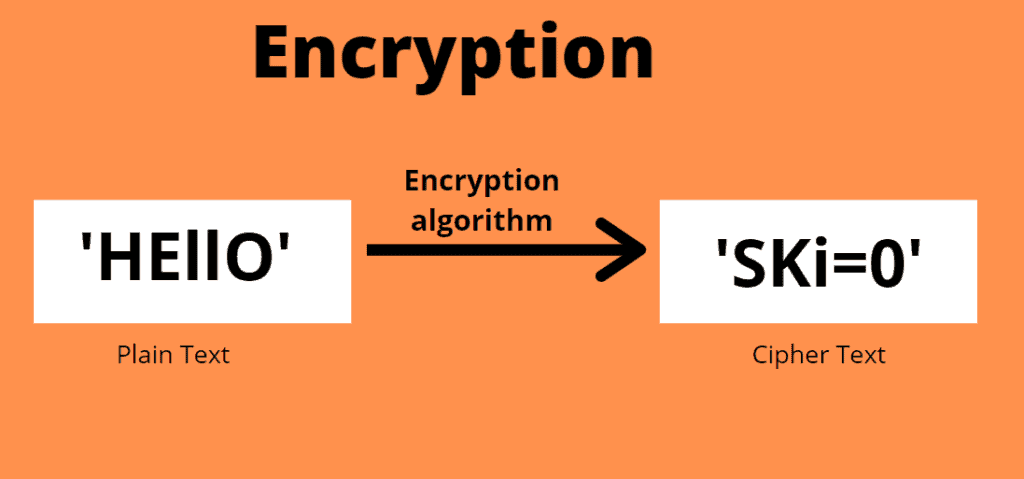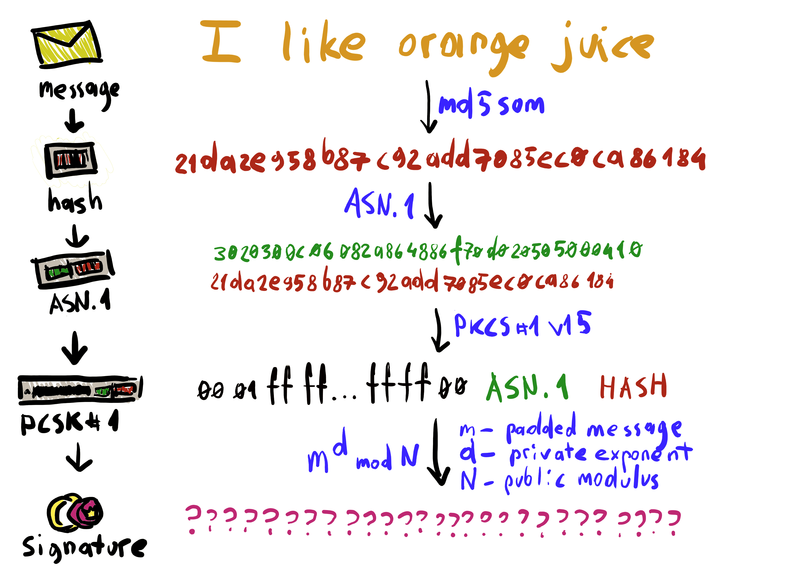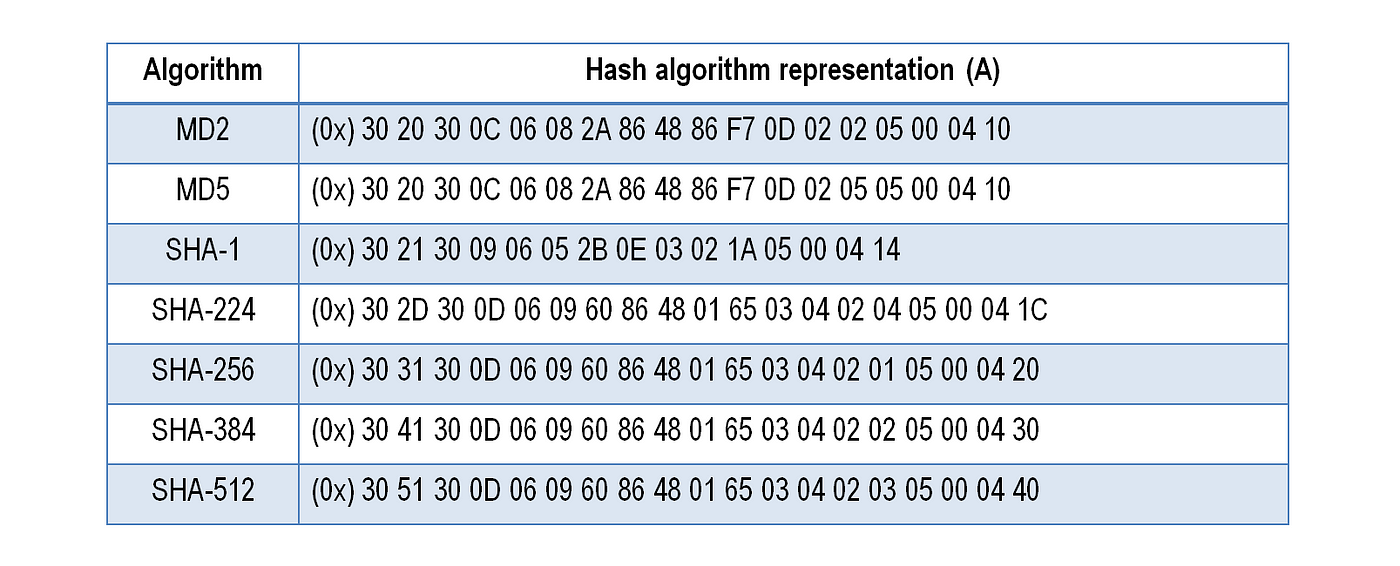
So How Does Padding Work in RSA?. Basically, PKCS#v1.5 is bad, OAEP is… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

1 Lect. 13 : Public Key Encryption RSA ElGamal. 2 Shamir Rivest Adleman RSA Public Key Systems RSA is the first public key cryptosystem Proposed in. - ppt download

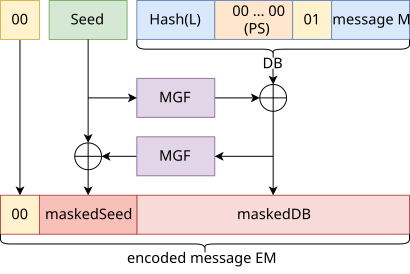
rsa pss - Why does PSS produce an EM message that's almost as long as the modulus? - Cryptography Stack Exchange

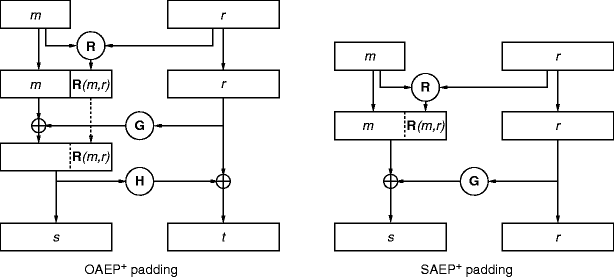
Wonk post: chosen ciphertext security in public-key encryption (Part 2) – A Few Thoughts on Cryptographic Engineering
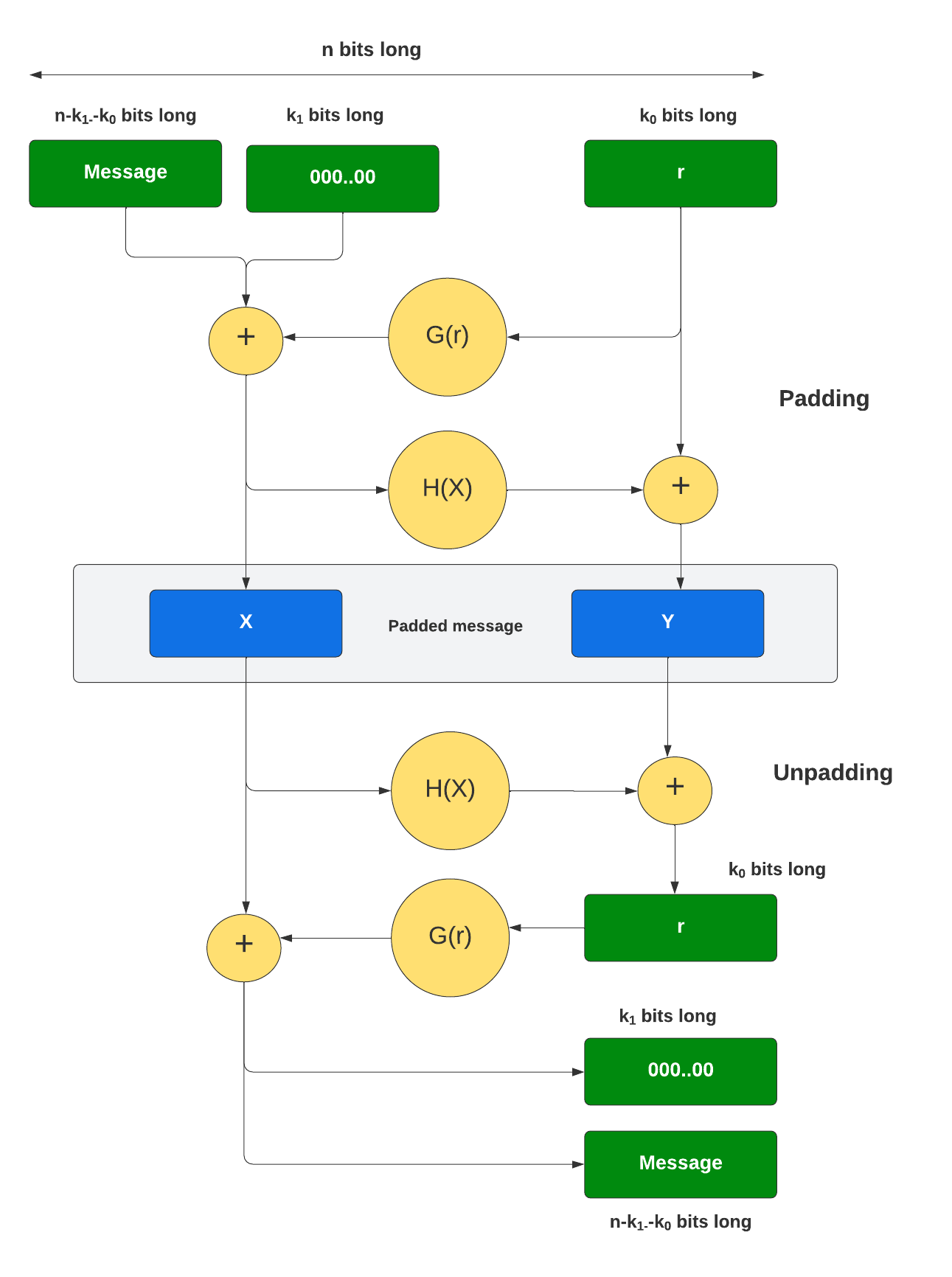
So How Does Padding Work in RSA?. Basically, PKCS#v1.5 is bad, OAEP is… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

rsa - Why PS does differ between PKCS1 v1.5 padding for signature and for encryption? - Cryptography Stack Exchange